Recently we added the Citrix Gateway connector for Exchange ActiveSync (formerly XenMobile NetScaler Connector) to a customer environment, with the intention of giving only known smartphones access to ActiveSync. The definition of known in this case, is a smartphone enrolled within Citrix Endpoint Management (formerly XenMobile). After some testing, we switched on “Blocking Mode” on the Gateway connector for Exchange ActiveSync and indeed all the ActiveSync traffic was nicely regulated. Only connections from device which existed in the Endpoint Management database were allowed access to ActiveSync. The check if a email client is allowed access is done based on the ActiveSync ID, which should be unique for every device.
Just to clarify, a short explanation how the Gateway connector for Exchange ActiveSync works. The Citrix Gateway connector for Exchange ActiveSync is connected to the Endpoint Management server(s) and periodically graps all ActiveSync ID’s. All the grapped ActiveSync ID’s are stored locally on the Gateway connector for Exchange server, in a .xml file. Depending you installation folder and provider name it’s stored on the Gateway connector for Exchange Server in : “%InstallFolder%\XenMobile NetScaler Connector\config\%ProviderName%.xml”
Depending your Endpoint Management ActiveSync Gateway configuration devices can be allowed or denied access based on several rules.
A complete set of rules is available on the Citrix Docs site
https://docs.citrix.com/en-us/xenmobile/server/provision-devices/activesync-gateway.html
Devices which are blocked are marked with a orange AS icon:
Back to the Gateway connector for Exchange ActiveSync Server itself! The XenMobile NetScaler Connector Service decides which ActiveSync ID should be allowed or denied access based on the file %ProviderName%.xml in combination with local StaticAllow/Deny rules.
Although everything seemed to work fine, an user reported he was able to access ActiveSync on a smartphone, which was not registered within Endpoint Management. This sounded like a breach of security which needed some further investigation. After analyzing the log files we were able to confirm the rogue smartphone was indeed allowed access to ActiveSync, although the ActiveSync ID was nowhere to be found in Endpoint Management.
So how was this possible ? We noticed the rogue smartphone was allowed access based on the Username, not the ActiveSync ID. Somehow the %ProviderName%.xml file, which was used to decide who is allowed or denied access not only contained ActiveSync ID’s, but for some users also contained their username.
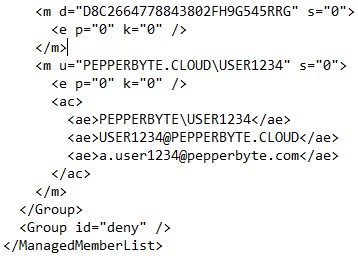
It didn’t took us long to notice that all the usernames belonged to Android users. So we did some additional testing and indeed if we would enroll an iOS smartphone only the ActiveSync ID was registered in %ProviderName%.xml. In case an Android user enrolled a smartphone, both ActiveSync ID and username were registered in %ProviderName%.xml. So what’s was the difference between iOS and Android?
In Endpoint Management one of the ActiveSync Gateway settings is called “Send Android domain users to ActiveSync Gateway”, which was enabled in our case.
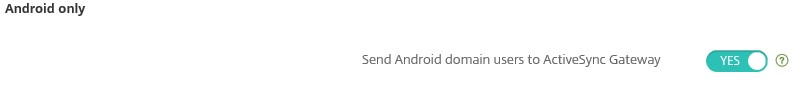
This option was enabled, because according to the Citrix Docs it should be enabled in case Android smartphones are being used.

We did some testing and changed the setting “Send Android domain users to ActiveSync Gateway” to NO. Soon after the change all usernames disappeared from %ProviderName%.xml and only ActiveSync ID’s were available. This sounded hopeful, but why does this option exists?
We contacted Citrix Support to confirm our findings and to answer the question why this special option existed. We were told the option “Send Android domain users to ActiveSync Gateway” should indeed be switched off, to prevent a security breach. Although Android smartphones are used in our environment, we didn’t need to enable this option. This option has been used in legacy versions of the product, but isn’t necessary for the latest version we were running.
So after the confirmation we received from Citrix Support we safely disabled the option “Send Android domain users to ActiveSync Gateway” and access to ActiveSync was only allowed based on ActiveSync ID!




